




The 22nd International Conference on Engineering of Complex Computer Systems (ICECCS 2017) will be held on November 6-8, 2017, Fukuoka, Japan. Complex computer systems are common in many sectors, such as manufacturing, communications, defense, transportation, aerospace, hazardous environments, energy, and health care. These systems are frequently distributed over heterogeneous networks, and are driven by many diverse requirements on performance, real-time behavior, fault tolerance, security, adaptability, development time and cost, long life concerns, and other areas. Such requirements frequently conflict, and their satisfaction therefore requires managing the trade-off among them during system development and throughout the entire system life. The goal of this conference is to bring together industrial, academic, and government experts, from a variety of user domains and software disciplines, to determine how the disciplines' problems and solution techniques interact within the whole system. Researchers, practitioners, tool developers and users, and technology transition experts are all welcome. The scope of interest includes long-term research issues, near-term complex system requirements and promising tools, existing complex systems, and commercially available tools.
| November 6th (Monday) | |
| Morning | |
| 8:45 | Registration |
| 9:20 - 9:30 | Opening |
| 9:30 - 10:30 | Keynote I (Chair: Zhenjiang Hu) |
| Verified Secure Routing: The Verified Scion Project (slides) David Basin (ETH Zurich, Switzerland) |
|
| 10:30 - 11:00 | Coffee Break |
| 11:00 - 12:20 | Session 1: Formal Method I (Chair: Jianjun Zhao) |
| Efficient Parameter Synthesis Using Optimized State Exploration Strategies Hoang Gia Nguyen, Étienne André and Laure Petrucci |
|
| Integrating Tools: Co-Simulation in UPPAAL using FMI-FMU Peter Gjøl Jensen, Kim Guldstrand Larsen, Axel Legay and Ulrik Nyman |
|
| Towarding Solving Decision Making Problems Using Probabilistic Model Checking (Short) Ling Shi, Shuang Liu, Jianye Hao, Jun Yang Koh, Zhe Hou and Jin Song Dong |
|
| 12:20 - 14:00 | Lunch |
| Afternoon | |
| 13:50 - 15:20 | Session 2: Formal Methods II (Chair: Naoyasu Ubayashi) |
| Extending ERS for Modelling Dynamic Workflows in Event-B Dana Dghaym, Michael Butler and Asieh Salehi Fathabadi |
|
| TLSsem: A TLS Security-Enhanced Mechanism against MITM Attacks in Public WiFis Wei Yang, Xiaohong Li, Zhiyong Feng and Jianye Hao |
|
| Reachability Analysis of Self Modifying Code Tayssir Touili and Xin Ye |
|
| 15:20 - 15:50 | Coffee Break |
| 15:50 - 17:20 | Session 3: IoT/CPS (Chair: Jing Xu) |
| Distributed Object-Oriented Design of Autonomous Control Systems for Connected Vehicle Platoons Sebti Mouelhi, Daniela Cancila and Amar Ramdane-Cherif |
|
| BigrTiMo-A Process Algebra for Structure-aware Mobile Systems Wanling Xie and Huibiao Zhu |
|
| Study of Software-Related Causes in the FDA Medical Device Recalls Zhicheng Fu, Chunhui Guo, Zhenyu Zhang, Yu Jiang, Lui Sha and Shangping Ren |
|
| 18:00 - 20:00 | Reception (on the first floor of the conference building) |
| November 7th (Tuesday) | |
| Morning | |
| 9:00 | Registration |
| 9:30 - 10:30 | Keynote II (Chair: Jianjun Zhao) |
| Exploring Similar Code - From Code Clone Detection to Provenance Identification (slides) Katsuro Inoue (Osaka University, Japan) |
|
| 10:30 - 11:00 | Coffee Break |
| 11:00 - 12:30 | Session 4: Knowledge and Software Engineering (Chair: Xiaohong Li) |
| Learning Likely Invariants to Explain Why a Program Fails Long H. Pham, Jun Sun, Ly Ly Tran Thi, Jingyi Wang and Xin Peng |
|
| Search-based Uncertainty-wise Requirements Prioritization Yan Li, Man Zhang, Tao Yue, Shaukat Ali and Li Zhang |
|
| Enhancing Knowledge Sharing in Stack Overflow via Automatic External Web Resources Linking Sa Gao, Zhenchang Xing, Yukun Ma, Deheng Ye and Shang-Wei Lin |
|
| 12:30 - 14:00 | Lunch |
| Afternoon | |
| 14:00 - 15:20 | Session 5: Design and Analysis I (Chair: Lei Ma) |
| A Composition Mechanism for Refinement-Based Methods Thai Son Hoang, Dana Dghaym, Colin Snook and Michael Butler |
|
| Class Modularization Using Indirect Relationships Junha Lee, Dae-Kyoo Kim and Sooyong Park |
|
| Model Driven Method to Design and Analyze Secure Architectures of Systems-of-Systems (Short) Jamal El Hachem, Tarek Al Khalil, Vanea Chiprianov, Ali Babar and Philippe Aniorte |
|
| 15:20 - 15:50 | Coffee Break |
| 15:50 - 17:20 | Session 6: Design and Analysis II (Chair: Walter Binder) |
| Formal Modeling and Automatic Code Synthesis for Robot System (Short) Xinxin Li, Rui Wang and Yu Jiang |
|
| A Unified Framework for Throughput Analysis of Streaming Applications under Memory Constraints Xue-Yang Zhu |
|
| Evaluating Suitability of Applying Blockchain (Short) Sin Kuang Lo, Xiwei Xu, Yin Kia Chiam and Qinghua Lu |
|
| Speeding up Type-specific Instrumentation for the Analysis of Complex Systems (Short) Andrea Rosà and Walter Binder |
|
| 18:00 - 20:30 | Banquet (in San Shiro Restaurant) |
| November 8th (Wednesday) | |
| Morning | |
| 9:00 | Registration |
| 9:30 - 10:30 | Keynote III (Chair: Baowen Xu) |
| Cyber-security, The Journey from Formal Methods, Program Analysis to Data Analytics (slides) Yang Liu (Nanyang Technological University, Singapore) |
|
| 10:30 - 10:50 | Coffee Break |
| 10:50 - 12:10 | Session 7: Other Short Papers (Chairs: Haibo Yu and Zhe Hou) |
| Multi-modeling approach to performance engineering of Cyber-Physical Systems design (Short) Lorenzo Pagliari, Raffaela Mirandola and Catia Trubiani |
|
| Software Reliability Modeling and Analysis via Kernel-based Approach (Short) Kei Okumura, Hiroyuki Okamura and Tadashi Dohi |
|
| Decomposition and Collaboration of Industrial Control System with Resource Constraints (Short) Ju Li, Jiawen Xiong, Xia Mao, Jianqi Shi, Xin Ye and Yanhong Huang |
|
| Functional Requirements-Based Automated Testing for Avionics (Short) Youcheng Sun, Martin Brain, Daniel Kroening, Andrew Hawthorn, Thomas Wilson, Florian Schanda, Francisco Javier Guzmán Jiménez, Simon Daniel, Chris Bryan and Ian Broster |
|
| 12:10 - 12:20 | Closing |
| 12:20 - 13:20 | Lunch |
Over the past several years, we have seen a rapid rising emphasis on design, implement and manage complex computer systems which are present in every aspect of human activities, such as manufacturing, communications, defense, transportation, aerospace, hazardous environments, energy, and health care. The complex computer systems are frequently distributed over heterogeneous networks and processing large amount data. Complexity arises from many factors, including the dynamic environments and scenarios these systems operate in; demanding and sometimes conflicting requirements in functionality, efficiency, scalability, security, dependability and adaptability; as well as the large variation in development methodology, programming languages and implementation details. The key issues in these systems include performance, real-time behavior, fault tolerance, security, adaptability, development time and cost, and long life concerns.
The goal of this conference is to bring together industrial, academic, and government experts, from a variety of application domains and software disciplines, to discuss how the disciplines' problems and solution techniques interact within the whole system. Researchers, practitioners, tool developers and users, and technology transfer experts are all welcome. The scope of interest includes long-term research issues; near-term requirements and challenges; established complex systems; emerging promising tools; and retrospective and prospective reflections of research and development into complex systems.
Authors are invited to submit papers describing original, unpublished research results, case studies and toolsed research results, case studies and tools. Papers are solicited in all areas related to complex computer-based systems, including the causes of complexity and means of avoiding, controlling, or coping with complexity. Topic areas include, but are not limited to:
Different kinds of contributions are sought, including novel research, lessons learned, experience reports, and discussions of practical problems faced by industry and user domains. The ultimate goal is to build a rich and comprehensive conference program that can fit the interests and needs of different classes of attendees: professionals, researchers, managers, and students. A program goal is to organize several sessions that include both academic and industrial papers on a given topic and culminate panels to discuss relationships between industrial and academic research.
Full papers are divided into two categories: Technical Papers and Experience Reports. The papers submitted to both categories will be reviewed by program committee members, and papers accepted in either category will be published in the conference proceedings. Technical papers should describe original research, and experience reports should present practical projects carried out in industry, and reflect on the lessons learnt from them.
Short paper submissions describe early-stage, ongoing or PhD research. All short papers will be reviewed by program committee members, and accepted short papers will be published in the conference proceedings.
Submitted manuscripts should be in English and formatted in the style of the double-column CPS format. Full papers should not exceed 10 pages, and short papers should not exceed 4 pages, including figures, references, and appendices. All submissions should be in PDF format. Submissions not adhering to the specified format and length may be rejected immediately, without review.
Please prepare your manuscripts in accordance to the CPS guidelines: http://www.ieee.org/conferences_events/conferences/publishing/templates.html.
We invite all prospective authors to submit their manuscripts via the ICECCS'17 portal, hosted on EasyChair https://easychair.org/conferences/?conf=iceccs2017
The conference proceedings will be published by Conference Publishing Services (CPS) and submitted for EI indexing.
As software systems are getting increasingly complex, we need new methods and tools to create and maintain them.
WOCSE '17 aims at bringing together researchers from academia and industry to present and discuss novel approaches to engineering complex systems.
In addition to the research track (see separate CFP), the 16th IEEE International Working Conference on Source Code Analysis and Manipulation (SCAM 2016) will also feature an Engineering Track. This track welcomes six-page papers that report on the design and implementation of tools for source code analysis and manipulation, as well as libraries, infrastructure, and the real world studies enabled by these advances. To be clear, this is not the addition of a new track to SCAM, which will remain a two track conference, but a significant expansion to the scope of the tools track of previous SCAMs.
What artefacts qualify as “engineering track” material?
A successful SCAM engineering track paper should:
Optionally (and encouraged):
Note that the submission length has a limit of six pages, compared to the two to four pages of traditional tool demo papers. This gives authors enough space to discuss artefact motivation, design, and use cases in much more detail. For example, a use case would be well illustrated by a demo scenario with screenshots. The papers should be submitted electronically via the conference web site.
Each submission will be reviewed by at least three members of the engineering track program committee. Authors of accepted papers will be required to present their artefacts at the conference. All accepted engineering track papers will be published in the conference proceedings. The key criterion for acceptance is that the paper should (a) follow the above mentioned guidelines and (b) make an original contribution that can benefit practitioners in the field now and/or others designing and building artefacts for source code analysis and manipulation. The artefacts can be in an early research prototype or a polished product ready for deployment. Papers about commercial products are allowed, as long as the guidelines described above are followed.
Videos and other demo material may be taken into account by reviewers as they review the paper. However, such material will not become part of the permanent record of the conference, so the paper should be self contained. In order to preserve the anonymity of the reviewers, such material should be hosted on an anonymous public source (e.g., youtube), or made available in such a way that the tools chair can download them once and redistribute them to reviewers.
All accepted papers will appear in the proceedings which will be published by the IEEE Computer Society Press.
Six pages IEEE format and can be submitted via EasyChair. Please use the IEEE templates in preparing your manuscripts:
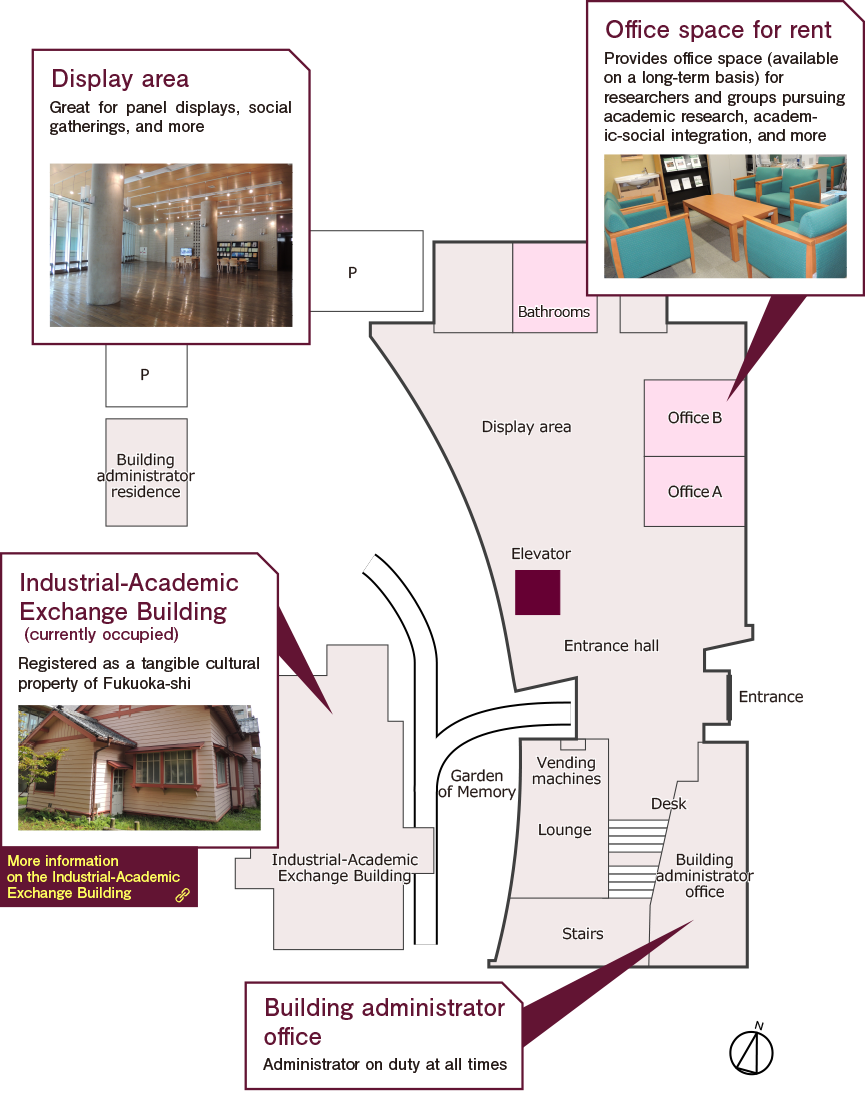
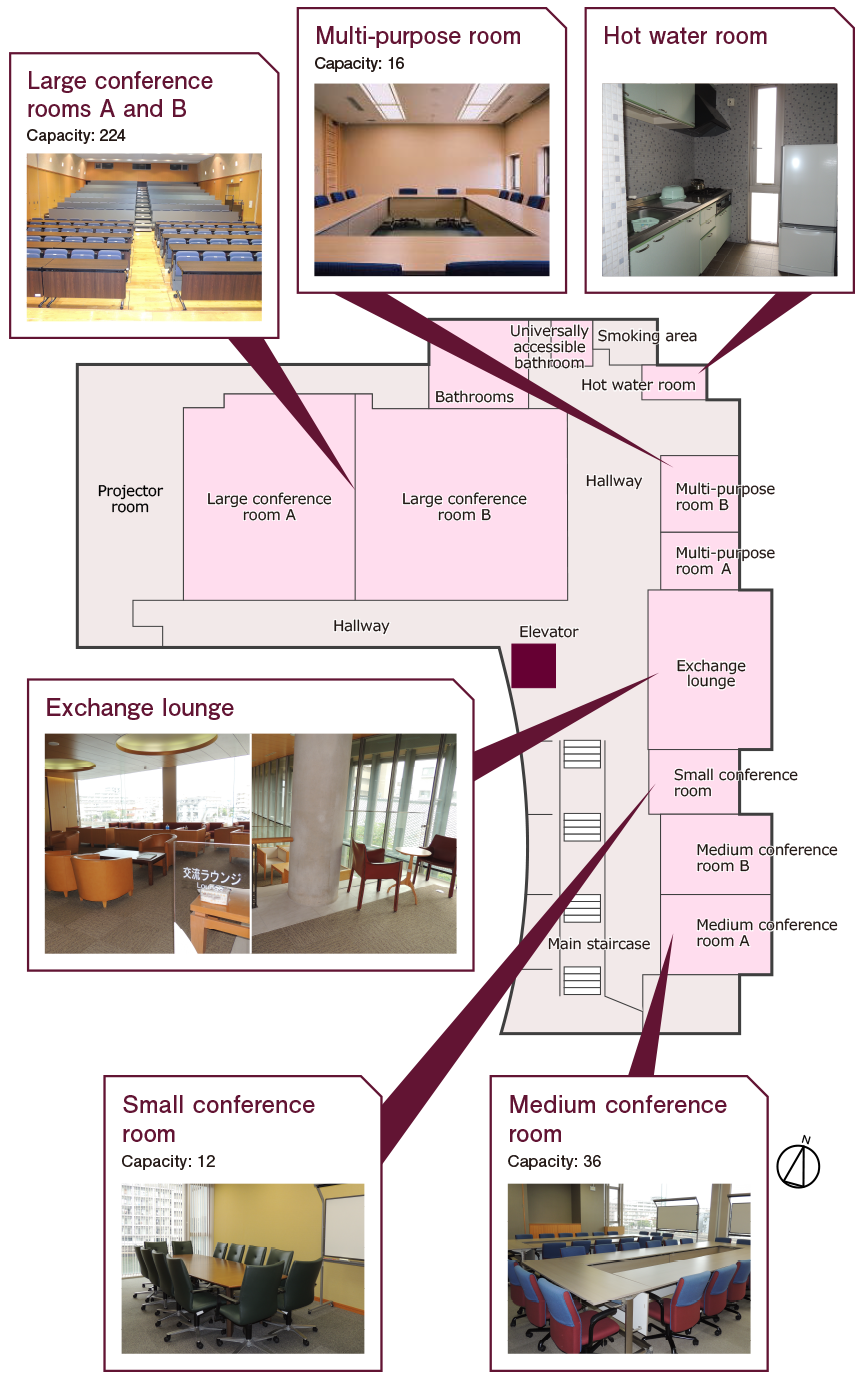
ICECCS 2017 will take place at the Nishijin Plaza of Kyushu University, Fukuoka, Japan.
2-16-23 Nishijin, Sawara-ku, Fukuoka-shi, Fukuoka-ken
814-0002 Japan




There are many hotels in Fukuoka from which you can quickly and easily access the conference venue by the public transportation, but the following list gives a few hotels near the conference venue. November is one of the best seasons in Japan and hotels tend to be very busy. If you plan to attend the conference, it will be good if you can book your hotels as early as you can. For hotel reservation, please directly use the following hotel webpages or directly contact with the hotels.
You can also use Booking.com to book your hotels in Fukuoka as well.
| Hotel Name | Time to walk to conference venue | Hotel Website |
|---|---|---|
| Twins Momochi | 12 mins | Link (Japanese only) |
| Heiwadai Hotel 5 | 12 mins | Link |
| The Residential Suites Fukuoka | 12 mins | Link |
| Hilton Fukuoka Sea Hawk | 11 mins | Link |
The subway line provides 5 minutes access from the airport to downtown (i.e.,Hakata station or Tenjin station) about 10 minutes.
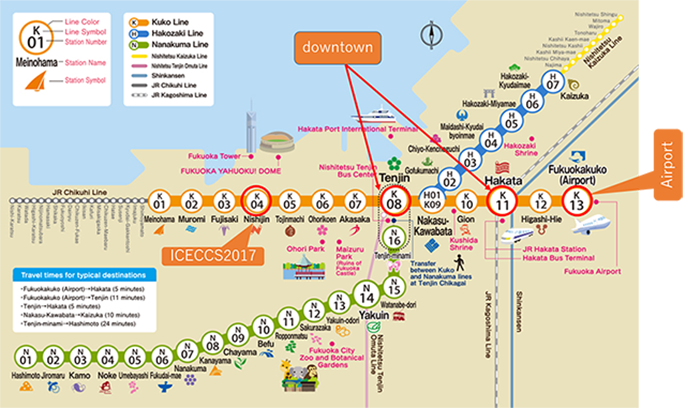
From Fukuoka Airport or downtown to the nearest subway station of ICECCS2017 venue
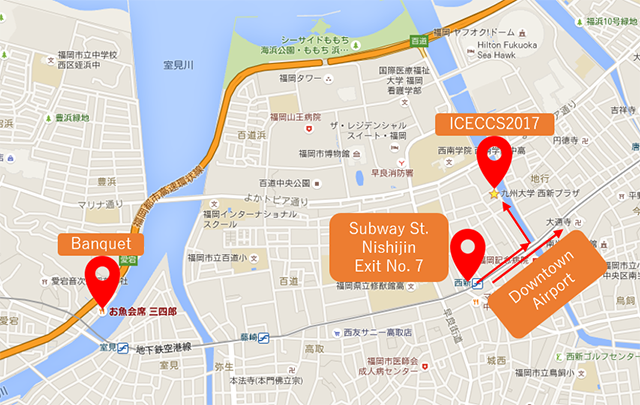
From Nishijin subway station to ICECCS2017 Venue
Ramen is a kind of noodle dish. Its origin is Chinese noodle but it has been localized for a hundred years. In Fukuoka, you can eat many kinds of Ramen, of which tonkotsu ramen is one of the most popular variation of ramen.
Since Fukuoka is a coastal city, you can enjoy a variety of seafood. Of cource, you can eat sushi or sashimi. Mentaiko (eggs of Alaskan Pollack) is a typical food of Fukuoka.
Motsunabe is Fukuoka-local dishes classified to nabemono. In motsunabe, beef or pork offal is used instead of chicken and its soup is spicy.
Kushiyaki is the general term for grilled/fried things on skewers. Chicken is some of the most popular, in that cases, Kushiyaki is also called "yakitori".
You can find information of restaurants at Gurunavi.




Please consult with your nearest Japanese embassy/consulate or your travel agency for the visa and entry requirements. For those who need a visa to travel to Japan, an invitation letter for visa can be issued by local organizers. Please send all requests to haibo_yu@sjtu.edu.cn with the following information:
Note that we can only provide invitation letters for visa to participants that have paid their registration fees. More details on Japan visa requirements can be found at here.
Registration for ICECCS 2017 is now open at Online Registration Site.
Each accepted paper must have at least one author registered at a REGULAR rate(80,000JPY). Papers for which the only registered authors are students must have one of the students register at the REGULAR rate.
The registration deadline for authors is 21 September 2017 The early registration deadline is 15 October 2017, and the late registration deadline is 3 November 2017.
| Early | Late | on-site | |
|---|---|---|---|
| Regular | 80,000 JPY | 95,000 JPY | 100,000 JPY |
| PC member | 70,000 JPY | 85,000 JPY | 90,000 JPY |
| Student | 60,000 JPY | 75,000 JPY | 80,000 JPY |
*ICECCS Registration Includes: ICECCS attendance including Lunch Monday through Wednesday, Reception on Sunday, Banquet on Tuesday, and ICECCS Proceedings.
Notification of cancellation must be made in writing (by email) to the Conference Secretariat (iceccs17@conferenceservice.jp). Cancellations will be accepted until Oct. 15, Sun. 23:59. When making a reimbursement, the Conference Secretariat will retain JPY 10,000 from prepaid registration fee as a processing fee. After Oct. 15, Sun. 24:00, no refunds will be made for any reasons.
If you have any questions about the registration, please contact the Conference Secretariat (iceccs17@conferenceservice.jp).

Routing is at the heart of the Internet and has been a continual source of security problems since its expansion in the 1980s. SCION is a new approach to the Internet, which offers dramatically better security properties than we currently have. We describe a collaborative effort, the Verified Scion Project, at ETH Zurich that aims to verify Scion, going the full distance from high-level network-wide properties down to the code running on SCION routers. We will explain the issues involved, the approach we take, the progress we have made, and perspectives for the future.
The work reported on is joint work between three groups at ETH Zurich: my Information Security Group, the Network Security Group of Adrian Perrig, and the Programming Methodology Group of Peter Mueller.

Code clone analysis is an activity to find similar code snippets in source code. Nowadays it becomes one of popular analyses characterizing redundancy and maintainability of source code. It has been studied for more than 20 years, and it is still a very active and attractive research field in Software Engineering. In this talk, we will present history and evolution of our research activities on code clone and related areas. Starting from an industry request for code maintenance, we have developed various tools and applied them to various fields. We will show also our current and future direction toward identifying code provenance in huge and complex ecosystem of Open Source Software.

Cyber-security is a complex system research, which requires the knowledge across all layers of the computer architecture. In this talk, I would like to share our attempts to solve security problems using various techniques. Starting from formal methods, we have applied formal modeling and reasoning to security designs and implementations on the topics related to security protocols, virtualization systems and Android apps. These efforts lead to our recent research project "Securify: A Compositional Approach of Building Security Verified System", which aims at building secure and verifiable systems ground-up. Security verification and building attack-free systems are very challenging tasks in the view of the size and the complexity of the systems. To solve the scalability problem, we start to explore various program analysis techniques to enhance the state-of-the-art malware and vulnerability detection, which generates encouraging results in Javascript/Android malware and binary vulnerabilities hunting. Along the way, we have collected sizable malware/vulnerabilities samples, which are further used to improving security analysis, understand the security trend, attack attribution/correlation and eventually provide high-level intelligence.
Dr Liu Yang graduated in 2005 with a Bachelor of Computing (Honours) in the National University of Singapore (NUS). In 2010, he obtained his PhD and started his post doctoral work in NUS, MIT and SUTD. In 2011, Dr Liu is awarded the Temasek Research Fellowship at NUS to be the Principal Investigator in the area of Cyber Security. In 2012 fall, he joined Nanyang Technological University as a Nanyang Assistant professor. He is currently an associate professor and the director of the cybersecurity lab in NTU.
Dr. Liu specializes in software verification, security and software engineering. His research has bridged the gap between the theory and practical usage of formal methods and program analysis to evaluate the design and implementation of software for high assurance and security. His work led to the development of a state-of-the-art model checker, Process Analysis Toolkit (PAT). This tool is used by research institutions in over 80 countries for research and education. By now, he has more than 150 publications in top tier conferences and journals and is leading an active research team working on various cybersecurity problems.
Banquet
The banquet will be held Sunday night at 7pm @ the Boxcar Arcade, less than a 10 minute walk from the convention center. The Boxcar features over 70 original games (e.g., Tetris, Mortal Kombat, NBA Jam, etc.), pinball, air hockey, and shuffle board that attendees can play while socializing. The evening will feature an informal spread from The Pit, featuring BBQ AND excellent vegetarian options, and of course a selection from Boxcar’s rotating 24 craft drafts.
Post-Conference Bike Ride
On the Tuesday following the conference (Oct. 4th) there will be a group bike ride from the conference venue to the Trophy Brewery, an approximately 3.2 mile (5.15 km) trip in one direction. More info and signup on the ICSME social events page.